6.3 KiB
6.3 KiB
Exploitation
- exploit: code or technique that a threat uses to take advantage of a vulnerability
- why exploitation?
- validating vulnerabilities
- assess impact
- prioritise fixes to vulnerabilities that can exploited
- test incident response
- exploited machine can work as pivot point
- risks
- system downtime
- system disruption
- data loss
- general bad things
- always verify exploit is allowed by Rules of Engagement
- most frequent initial access vectors
- valid account usage, e.g. obtaining valid credentials
- phishing
- exploiting remote vulnerabilities
- external remote services (e.g. managed filetransfer services)
Categories
- remote exploit: attack a service listening on the network
- client-side exploit: attack a client application that fetches content from a server
- local privilege escalation exploit: attack to gain higher privileges on
machine attacker is already on
- often not patched quickly as they're not considere critical
- various types
- race conditions
- kernel exploits
- local exploit of high-privileged program or service
- hardware and firmware exploits
- cryptographic exploits
Client-side exploit
- wait for target user to access infected file on attacker-controller server
- target machine opens connection with attacker
- doesn't get blocked by firewall
- requires user interaction to run client program
- usually requires privilege escalation
- companies often wait too long to update software -> effective strategy
- exploit kits
- sophisticated delivery method for malware
- can be rented as a SaaS
- automatically inspects host for vulnerabilities
- gate servers to only forward vulnerable hosts to infected page
Pentesting
- email campaign
- send phishing mails to employees and exploit those that click
- risk of going out of scope (e.g. forwarding the email)
- better: spear-phishing emails with links or attachments
- only register how many clicks happened
- use controller company user that clicks link on purpose to see if exploit works
- combined this is a safer method that provides useful statistics
- send phishing mails to employees and exploit those that click
- identify software used by company
- ask target personnel
- analyse metadata from documents
- analyse cached DNS records
- have target personnel surf to testing systems ([www.gotya.org])
- assume very popular software is used (Adobe Reader, Microsoft Office...)
- let personnel run software inventory tool
- important to use representative machine
- don't use newly patched laptop
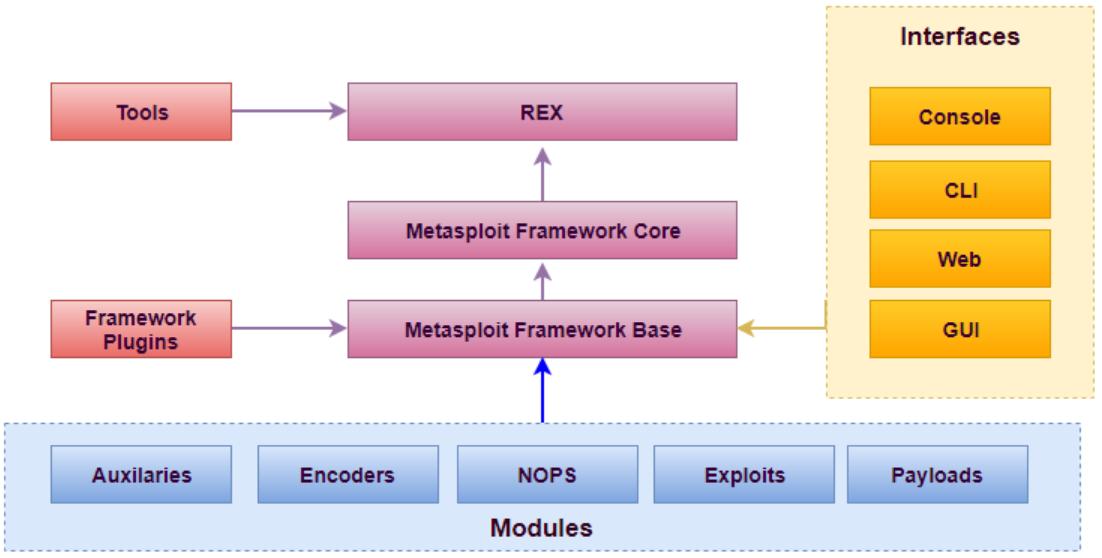
Metasploit
- free open-source exploitation framework
- types of modules
- exploit: technique that takes advantage of flaw in target
- payload: makes target do something the attacker wants (e.g. open
shell)
- single: standalone payload that does both functionality and communication (useful for low bandwidth)
- stager: part that establishes communication
- stage: implements a function using stager as communication channel
- auxiliary: other useful modules, e.g. port scanning
- post: used post-exploitation to reconfigure or plunder target (e.g. set up persistency)
- Jordan Peele's NOP instruction
- CPU instruction that does nothing
- buffer alignment: align code/payload in memory
- required when precies memory control is important
- useful in buffer overflow attacks
- sliding to payload (NOP sled): pad payload with NOPs to account for
innacurate memory accesses
- NOP slide ensure payload is executed if memory is accessed anywhere inside the sled
- stabilizing exploits: provide padding around exploits to stabilize memory access
- some commands
msfconsole: main REPL where the magic happensmsfrpcd: RPC daemon providing access to Metasploit's functionality- enables integration with other applications
msfvenom: tool to convert payloads to standalone executable files (optionally with detection evasion)
- PsExec
- Microsoft SysInternals tool for remote administration of hosts
- often exploited as it's very powerful
- data execution prevention (DEP)
- security feature in modern OSs
- only allows memory marked as executable to be executed
- can be enforced by hardware
- meterpreter
- interactive Metasploit interpreter
- payload acting as interactive shell running in-memory on exploited hosts
- not persisted
- leaves no trace
- no separate process created
- can migrate to other processes
- support database for persistent data
- exploits often provide shell access, not terminal
- interactive stuff doesn't work (e.g. password prompts)
- shell can be used to set up terminal (e.g. install SSH server)
antivirus evasion
- antivirus techniques
- signature: identify malware by comparing against a DB of known malware signatures
- heuristic: analyse behaviour and structure of code (statically?) (self-replication, touching weird files...)
- behavioral: actively monitor behavior in real-time dynamically
- sandboxing: run file in controlled environment to observe without harming system
- integrity checking: check integrity of system files and applications (periodically compare checksums)
- evasion tactics
- shut down antivirus
- ghost writing: insert dummy instructions that preserve behavior of
file
- simpler AVs simply compare checksums of fragments; modifying code with NOP instructions changes checksum and avoids matching checksums
- anti-emulation techniques: detect when running in sandbox and change behavior to be less suspicious
- obfuscation: encode or encrypt malware to avoid signature matching
- fileless malware: load malware directly into memory
- avoid file system changes checks
- by injecting into existing process, processing scanning checks are evaded
- no need to evade all AVs
- OSINT step can gather which AV is used
- exploits can be tailored to avoid specific AV