2.7 KiB
2.7 KiB
Scanning
- learn more about targets
- find potential attack openings
- addresses of live hosts
- network topologies
- OSs of hosts
- open ports
- services running on hosts
Network tracing
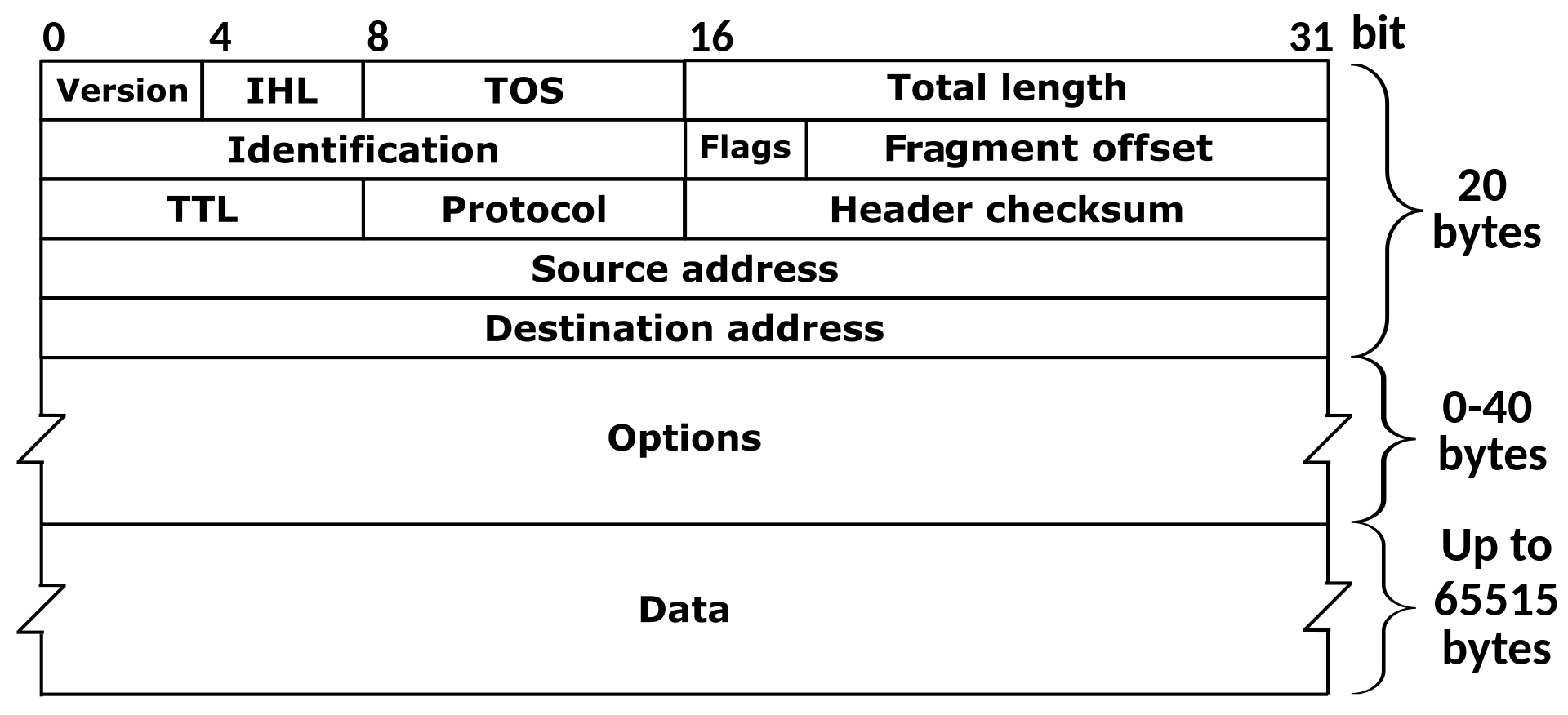
IPv4 and IPv6
- important IPv4 headers
- TTL: time to live
- tells us how many hops a package needed to make
- source and destination IP
- TTL: time to live
- IPv6 properties
- 128 bit addresses
- simpler than IPv4
tracing
- discover routes that packets take between systems
- allows constructing network diagrams
- sends ICMP/UDP/TCP packets with varying TTL
- requires routers to properly report dropped packets
- often disabled for performance/security reasons
tracerouteuseful tool- web-based tools also available
Scanning
- Nmap does it all
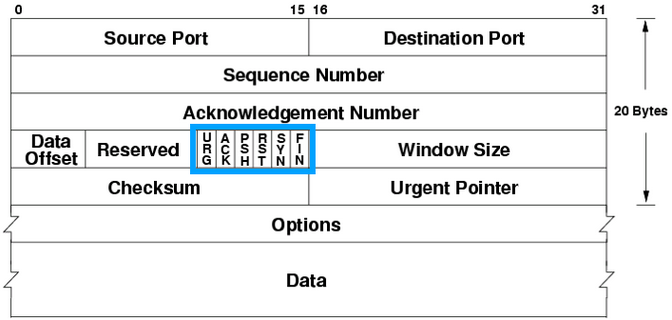
TCP
- 16-bit ports
- sequence and ack number for reliable in-order delivery
- control bots track state
- URG: urgent flag
- ACK: acknowledge earlier packets
- PSH (push): data should not be buffered
- RST: reset connection
- SYN: synchronisation, sends initial sequence number
- FIN: indicate session can be closed
- half-open port scanning
- only send SYN part of handshake
- listen for response
- SYN + ACK: port open
- RST + ACK: port closed or blocked
- ICMP port unreachable: likely blocked
- no response: likely blocked
- can take a while if no responses are sent
- large scans are bad
- limit scope of scan
- select subset of targets
- only scan well-known ports initially
- limit scan based on firewall information
- temporarily tweak firewall to speed up scans
- use parallel machines (be careful not to DoS)
- scanrand & zmap tools
- limit scope of scan
UDP
- send empty UDP datagram and listen
- UDP packet response: something is listening on target port
- ICMP port unreachable: likely blocked
- no response: multiple options
- port is blocked by firewall
- port only responds to specific format
ARP
- Address Resolution Protocol
- data link layer
- translates IPv4 addresses to MAC addresses
- scan local subnet for hosts
- lots of traffic
- can be detected by network intrusion detection systems (NIDS)
ICMP
- Internet Control Message Protocol
- used for diagnostic purposes
- error reporting
- router discovery
- redirect messages
- ping sweeps
- traceroute
- redirect messages expose network topology
- ICMP address mask requests: determine subnet used by target host