2.3 KiB
2.3 KiB
Introduction
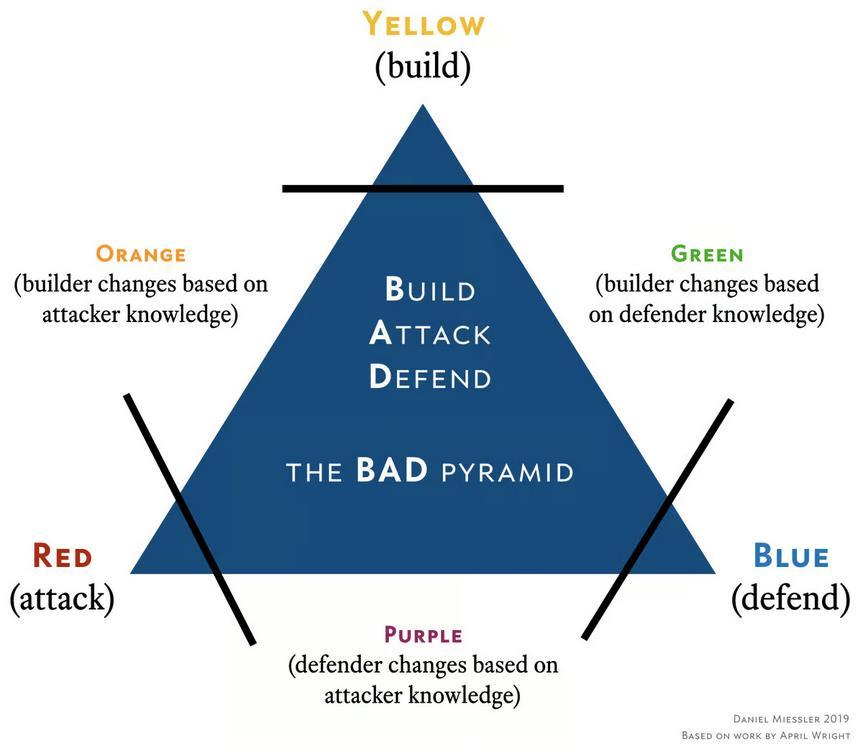
Teams involved in security
- red: attack team
- test effectiveness of security by performing attacks
- blue: defend team
- defend against attacks by constantly surveiling the network
- yellow: build team
- builds applications that can be used by the other teams
- sharing knowledge
- orange: builders learn from attackers
- green: builder learn from defenders
- purple: defenders learn from attackers
Penetration testing
Penetration testers <-> red teams
- penetration testing
- methodical approach
- limited by Rules of Engagement (restricted scope)
- 1-2 week engagement
- generally announced
- goal is to assess security of network and systems
- red team
- flexible approach
- anything goes (as long as it's legal)
- 1 week to 6 months engagement
- no announcement
- goal is to test general security posture of company
Penetrating testing <-> vulnerability assessments
- penetration testing
- find vulnerabilities, both automated and manually
- exploit them
- attempt to gather confidential data
- intended to go deeper and focus on technical issues
- vulnerability assessment
- find vulnerabilities through automated means
- don't exploit them or gather data
- broader and often includes explicit policy and procedure review
assumed breach exercise
- pentest where attackers are assumed to already be inside
- malware is dropped inside company boundaries
- getting caught not the end -> reset and try again
- Time To Detect (TTD): how long it takes to notice breach
- Time To Mitigate (TTM): how long it takes to perform corrective action
Useful resources
- MITRE: knowledge base of attack tactics and
techniques
- explanation of TTPs (Tactics, Techniques and Procecures)
- APT Groups and Operations: Google doc containing list of dangerous groups
- Cyber Fundamentals
- concrete measures on how to protect data and ensure safety in company
- four assurance levels
- five core functions
- identify
- protect
- detect
- respond
- recover