7.7 KiB
7.7 KiB
Scanning
- learn more about targets
- find potential attack openings
- addresses of live hosts
- network topologies
- OSs of hosts
- open ports
- services running on hosts
Network tracing
- discover routes that packets take between systems
- allows constructing network diagrams
- sends ICMP/UDP/TCP packets with varying TTL
- requires routers to properly report dropped packets
- often disabled for performance/security reasons
tracerouteuseful tool- web-based tools also available
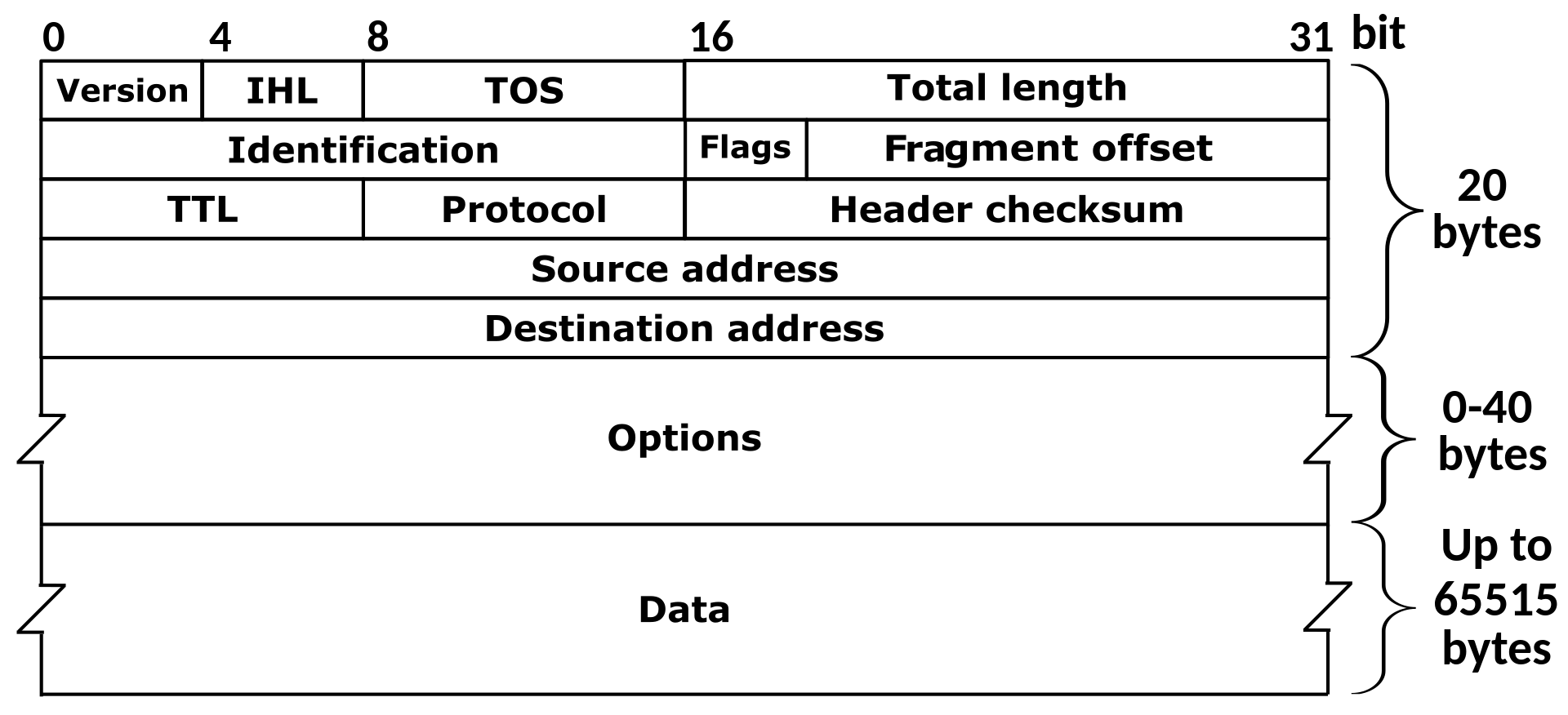
IPv4 and IPv6
- important IPv4 headers
- TTL: time to live
- tells us how many hops a package needed to make
- source and destination IP
- TTL: time to live
- IPv6 properties
- 128 bit addresses
- simpler than IPv4
Scanning
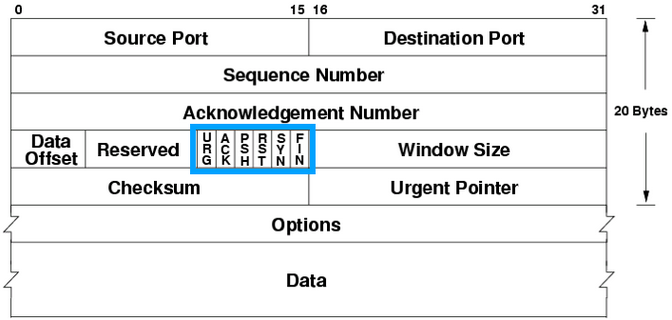
TCP
- 16-bit ports
- sequence and ack number for reliable in-order delivery
- control bots track state
- URG: urgent flag
- ACK: acknowledge earlier packets
- PSH (push): data should not be buffered
- RST: reset connection
- SYN: synchronisation, sends initial sequence number
- FIN: indicate session can be closed
- half-open port scanning
- only send SYN part of handshake
- listen for response
- SYN + ACK: port open
- RST + ACK: port closed or blocked
- ICMP port unreachable: likely blocked
- no response: likely blocked
- can take a while if no responses are sent
- large scans are bad
- limit scope of scan
- select subset of targets
- only scan well-known ports initially
- limit scan based on firewall information
- temporarily tweak firewall to speed up scans
- use parallel machines (be careful not to DoS)
- scanrand & zmap tools
- limit scope of scan
UDP
- send empty UDP datagram and listen
- UDP packet response: something is listening on target port
- ICMP port unreachable: likely blocked
- no response: multiple options
- port is blocked by firewall
- port only responds to specific format
ARP
- Address Resolution Protocol
- data link layer
- translates IPv4 addresses to MAC addresses
- scan local subnet for hosts
- lots of traffic
- can be detected by network intrusion detection systems (NIDS)
ICMP
- Internet Control Message Protocol
- used for diagnostic purposes
- error reporting
- router discovery
- redirect messages
- ping sweeps
- traceroute
- redirect messages expose network topology
- ICMP address mask requests: determine subnet used by target host
Nmap
- port scanner and all-in toolkit
- important tool when performing scanning
- TCP port scanning
- connect scan
- complete 3-way handshake
- can run without root
- not stealthy (connections can be logged)
- doesn't use nmap to craft packets
- syn scan/half-open scan
- runs as root
- only send initial SYN and listen for response
- detectable by firewall/NIDS
- ACK scan
- playing with control bits
- FIN scan: FIN bit of all packets set
- NULL scan: all bits set to 0
- Xmas tree scan: FIN, PSH, URG set
- Maimon scan: FIN and ACK set
- connect scan
- UDP scanning
- scans specific UDP ports
- sends protocol-specific messages to well-known ports
- firewall spotting
- generate packets with invalid TCP or UDP checksum
- targets will drop these
- firewalls don't always check checksum and will send a RESET/ICMP port unreachable instead
- allows detecting firewalls
- can also look for varying TTL values
- TTL on firewall RESET message will be higher as the firewall is closer
- full support for IPv6
- OS fingerprinting
- detect quirks of protocol behaviors for OS versions
- active: send special packets to detect behavior
- passive: observe patterns of network traffic (stealthy but less accurate)
- version scanning
- detect versions of services running on host
- send packets to specific service types that reveal version information
- useful for crafting exploits
Other stuff
- automated monitoring
- running nmap using cron can reveal changes in network
- tools like masscan well suited for this
- monitoring web applications also important
- HTTPScreenshot: take screenshots of websites
- EyeWitness: screenshots of webpages, RDP and VNC servers, tries to login with default credentials
- scanning cloud infrastructure
- badly configured S3
- buckets that allow writing without authorisation
- subdomain takeover allows attacker to take over bucket URL
- packet crafting
- sometimes very specific/controlled packets are required
- tools like Scapy allow crafting packets for various
protocols
- Python tool
- provides REPL to forge, send and receive packets
Vulnerability scanning
- process used to identify security weaknesses and vulnerabilities in a system,
network or application
- involves using automated tools to scan systems for known vulnerabilities and weaknesses
- critical component of a robust cybersecurity strategy
- automated scanning allows detecting problems before they're possibly exploited
- key aspects
- goal: identify and address security flaws before they're exploited
- scan types
- network scanning
- web app scanning
- host scanning
- process
- discovery: identify all relevant devices, systems and applications
- scanning: use automated tools to scan targets for known vulnerabilities
- analysis: analyse results for vulnerabilities and prioritize them
- reporting: generate report detailing results
- frequency: how often to perform scans
- compliance: many regulatory standards require regular vulnerability scanning
Methods
- Nmap Scripting Engine (NSE)
- allows extending nmap with Lua scripts
- greatly broadens scope of nmap
- nmap comes with a ton of ready-to-use scripts
- perfect for vulnerability scanning
- Tenable Nessus
- modern vulnerability scanner
- can detect tens of thousands of vulnerabilities
- free for personal use
- OpenVAS
- open-source vulnerability scanner
- less expansive than Nessus
Enumerating users
- process of retrieving list of usernames for system
- numerous methods
- public sources of information (websites, emails...)
- pentest: ask for list of users (grey box)
- Linux
- local:
/etc/passwd - remotely
finger @IP- query NIS or LDAP server if present
enum4linuxtool
- local:
- Windows
- list users using SMB session
- possible anonymously on older versions of Windows
- if single user is known, listing all users is possible
- list users using SMB session
Netcat
- netcat is useful
- general purpose TCP and UDP network tool
- installed basically everywhere
- used for setting up reverse shells among other things
- it's just a useful network tunnel